SCIENTIFIC AND COMPUTER DEVELOPMENT BLOG 1|2
|
An introduction to the Computer Algebra Systems (CAS)
By Martin Rupp
 "Other classes of CAS - available for PCs - allow more complex symbolic manipulations and computations, in what follows, we are going to detail what they can offer. A good list of CAS software can be found here.Several of these CAS are doing approximately the same thing as the CAS of the scientific calculators.More complex things that some of these CAS can do are the following:Computations with finite groups;Computations with finite fields, like polynomial fields over a finite field;Computations with tensors;Modular arithmetic;Number theory;Algebraic geometry computations;Symbolic solvers of complex classes of differential equations.“Read More
"Other classes of CAS - available for PCs - allow more complex symbolic manipulations and computations, in what follows, we are going to detail what they can offer. A good list of CAS software can be found here.Several of these CAS are doing approximately the same thing as the CAS of the scientific calculators.More complex things that some of these CAS can do are the following:Computations with finite groups;Computations with finite fields, like polynomial fields over a finite field;Computations with tensors;Modular arithmetic;Number theory;Algebraic geometry computations;Symbolic solvers of complex classes of differential equations.“Read More
|
Les principes théoriques de la cryptographie sur les courbes elliptiques
Par Martin Rupp
“Un grand nombre d'algorithmes cryptographiques utilisent les courbes elliptiques (le plus connu d’entre eux est ECDSA (voir [6])). Ces algorithmes sont réputés plus sûrs que d’autres algorithmes équivalents à base de structures mathématiques qui sont “plus classiques”. Ces algorithmes basés sur les courbes elliptiques peuvent consister en du chiffrement ou des signatures asymétriques mais les bases théoriques d'où elles proviennent sont souvent méconnues, voire totalement inconnues. En effet: quelles sont ces “courbes elliptiques”, et en quoi assurent-elles une garantie de sécurité à ces algorithmes ? Et comment doivent-elles concrètement être implémentées.”
Lire l'Article
|
A solution to the Fermi paradox
By Martin Rupp
 "The Fermi paradox states in essence that we seem to be desperately alone in the universe and that the Earth seems to be the only inhabited planet of the creation.There is an easy solution to that paradox.“Read More
"The Fermi paradox states in essence that we seem to be desperately alone in the universe and that the Earth seems to be the only inhabited planet of the creation.There is an easy solution to that paradox.“Read More
|
A brief overview of the challenges involved in key management for EMV personalization
By Martin Rupp
 "EMV personalization relates to the process of writing specific information to the chip of a payment card. These data are most often of cryptographic nature and involve extreme< security and confidentiality data transmission between the personalization devices and the chip of the cards. EMV personalization is ruled by a global document named the CPS, for ‘Common Personalization Specifications’.“Read More
"EMV personalization relates to the process of writing specific information to the chip of a payment card. These data are most often of cryptographic nature and involve extreme< security and confidentiality data transmission between the personalization devices and the chip of the cards. EMV personalization is ruled by a global document named the CPS, for ‘Common Personalization Specifications’.“Read More
|
Should We Really Start Preparing for Post-Quantum Crypto?
By Martin Rupp
 "With the arrival of the first quantum computers - while still imperfect,cryptologists from all around the world have started to ring the alarm bell: If a quantumcomputer is built, it has the ability to crack many of the widely used cryptography presentin everyday’s life in several industries, including the banking industries. Here we aim atpresenting facts regarding whether or not it is realistic to start already preparing for aPost-Quantum cryptographic migration.“Read More
"With the arrival of the first quantum computers - while still imperfect,cryptologists from all around the world have started to ring the alarm bell: If a quantumcomputer is built, it has the ability to crack many of the widely used cryptography presentin everyday’s life in several industries, including the banking industries. Here we aim atpresenting facts regarding whether or not it is realistic to start already preparing for aPost-Quantum cryptographic migration.“Read More
|
How to solve the Bridge and Torch problem using simulation
By Martin Rupp
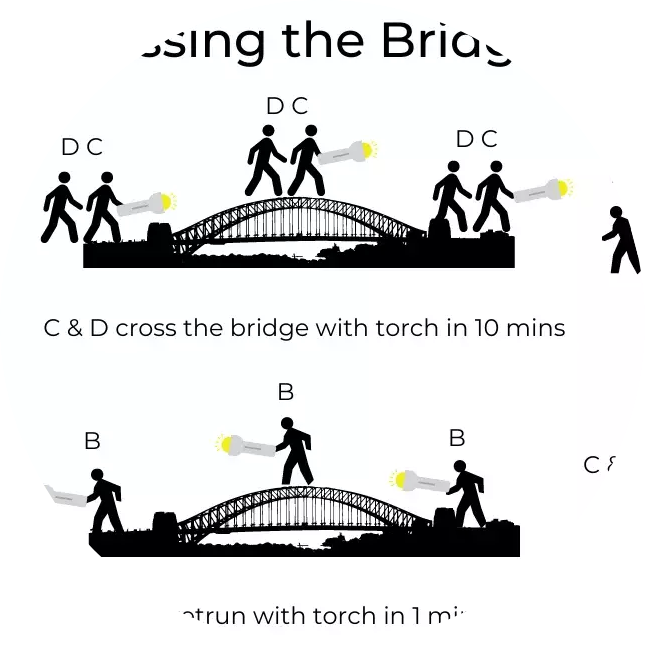 "In this article, we will show an example of a puzzle that can be solved using algorithmic an computer simulation.Puzzles are Common in recreational logic or mathematics. Some of them may be extremely hard to solve - or even impossible. Here we will consider an ‘elementary’ puzzle. That is to say, a puzzle where the space of the possible configurations is finite and where almost all of the data are known. We will show how to use elementary computer simulation to solve it“Read More
"In this article, we will show an example of a puzzle that can be solved using algorithmic an computer simulation.Puzzles are Common in recreational logic or mathematics. Some of them may be extremely hard to solve - or even impossible. Here we will consider an ‘elementary’ puzzle. That is to say, a puzzle where the space of the possible configurations is finite and where almost all of the data are known. We will show how to use elementary computer simulation to solve it“Read More
|
An overview of the different 3d printers technologies
By Martin Rupp
 "All through the ages, humanity has always dreamed of being able to reproduce objects and multiply them - as by magic, without the need for a complicated individual assembly.In fact making duplicate objects appear almost instantly is a recurrent fantasy andscience-fiction theme!Here we are! 3D printing is making almost that old dream come true and year after year, 3d printing becomes more and more sophisticated and can fidelly reproduce even the most difficultobjects!.
“Read More
"All through the ages, humanity has always dreamed of being able to reproduce objects and multiply them - as by magic, without the need for a complicated individual assembly.In fact making duplicate objects appear almost instantly is a recurrent fantasy andscience-fiction theme!Here we are! 3D printing is making almost that old dream come true and year after year, 3d printing becomes more and more sophisticated and can fidelly reproduce even the most difficultobjects!.
“Read More
|
Is India becoming the world’s next tech superpower?
By Martin Rupp
 "The recent events linked to COVID-19 have slightly changed our perception of the world. China, who used to be ‘the factory of the world’, the second economical power, has now somehow been downsized. Finally, Indian science publications are now gaining momentum, especially in the area of Artificial Intelligence.
“Read More
"The recent events linked to COVID-19 have slightly changed our perception of the world. China, who used to be ‘the factory of the world’, the second economical power, has now somehow been downsized. Finally, Indian science publications are now gaining momentum, especially in the area of Artificial Intelligence.
“Read More
|
Colonizing the Icy Moons in the Outer Solar System: A White Paper Mission Concept
By Bassem Sabra
 "This WP will elucidate a program to colonize the outer solar system by establishing continuous and sustainable human presence on the ice moons. All mission requirements are driven by human constraints.”Read More
"This WP will elucidate a program to colonize the outer solar system by establishing continuous and sustainable human presence on the ice moons. All mission requirements are driven by human constraints.”Read More
|
The main principles of the AES cryptographic algorithm
By Martin Rupp
“AES stands for “Advanced Encryption Standard''. This is a cryptographic algorithm primarily developed for and by normative bodies in the United States of America such as NIST. It is also often referred to as the algorithm Rijndael although the AES is actually a variant of the latter.”Read More Read French Version
|
Introduction to AI for machine language translation (RNN)
By Martin Rupp
“I  n this series of articles, we’ll show you how to use deep learning to create an automatic translation system. This series can be viewed as a step-by-step tutorial that helps you understand and build a neuronal machine translation.This series assumes that you are familiar with the concepts of machine learning: model training, supervised learning, neural networks, as well as artificial neurons, layers, and backpropagation.Before diving into specifics of the use of deep learning (DL) for translation, let’s have a quick look at machine translation (MT) in general.“Read More
n this series of articles, we’ll show you how to use deep learning to create an automatic translation system. This series can be viewed as a step-by-step tutorial that helps you understand and build a neuronal machine translation.This series assumes that you are familiar with the concepts of machine learning: model training, supervised learning, neural networks, as well as artificial neurons, layers, and backpropagation.Before diving into specifics of the use of deep learning (DL) for translation, let’s have a quick look at machine translation (MT) in general.“Read More
|
AFD Cards - Transition from 3DES to AES
By Martin Rupp
 “Here we will focus on fleet cards issued by banks and/or follow a payment card association scheme (Visa, MasterCard, etc.).We may refer to these fleet cards as “AFD” cards (or AFD-Fleet cards), where AFD stands for Automated Fuel Dispenser. Like traditional bank cards, these cards and the infrastructure behind them need to also consider moving from 3DES to AES if they already use a chip or are directly integrating AES if they are migrating to EMV.”Read More
“Here we will focus on fleet cards issued by banks and/or follow a payment card association scheme (Visa, MasterCard, etc.).We may refer to these fleet cards as “AFD” cards (or AFD-Fleet cards), where AFD stands for Automated Fuel Dispenser. Like traditional bank cards, these cards and the infrastructure behind them need to also consider moving from 3DES to AES if they already use a chip or are directly integrating AES if they are migrating to EMV.”Read More
|
The Atalla Secure Configuration Assistant and Concepts of HyperSecurity
By Martin Rupp
 “The notion of hyper-security in the era of Information Technology security and for the general security of computer systems is still an experimental concept. It is a set of ideas rather than a well-defined term. Here we shall define hyper-security simply as the sum of all security constraints of a system that involves physical security, cyber-security, ”Read More
“The notion of hyper-security in the era of Information Technology security and for the general security of computer systems is still an experimental concept. It is a set of ideas rather than a well-defined term. Here we shall define hyper-security simply as the sum of all security constraints of a system that involves physical security, cyber-security, ”Read More
|
Microsoft Windows is EAL4+ … What does it mean ?
By Martin Rupp
 “Common Criteria for Information Technology Security Evaluation or shortly, Common Criteria, is a security evaluation framework for computer systems, the result of the merge of several other ones, namely the ITSEC, CTCPEC and TCSEC”Read More
“Common Criteria for Information Technology Security Evaluation or shortly, Common Criteria, is a security evaluation framework for computer systems, the result of the merge of several other ones, namely the ITSEC, CTCPEC and TCSEC”Read More
|
Why NanoServer should not be used for containerization
By Martin Rupp
 “In this article we analyze why the Nano Server Operating System should not be used as a containerization solution.”Read More
“In this article we analyze why the Nano Server Operating System should not be used as a containerization solution.”Read More
|
Could teleportation technologies become a reality ?
By Martin Rupp
 “We all know the famous ‘beam me up Scotty !’ or “Scotty, energize !” sentences from the Star Trek series. By doing so, a group of people are usually instantly transported from one location to another location, going through any sort of obstacles.Of course this is a science-fiction topic but could it become a reality ? Here are some views about the subject as well as a list of a few techno-physical ways we could develop such teleportation Technologies. ”Read More
“We all know the famous ‘beam me up Scotty !’ or “Scotty, energize !” sentences from the Star Trek series. By doing so, a group of people are usually instantly transported from one location to another location, going through any sort of obstacles.Of course this is a science-fiction topic but could it become a reality ? Here are some views about the subject as well as a list of a few techno-physical ways we could develop such teleportation Technologies. ”Read More
|
An introduction to the serious games
By Martin Rupp
 “In this blog we are going to explore an unsuspected technological territory : the world of gaming technology applied for the military, law enforcement, education or even … research.What are we referring to? Video games can be very intensive, and they can provide a very immersive experience. Commercial video games almost always feature characters involved in war or fighting actions which makes them an ideal tool for … real military training.”Read More
“In this blog we are going to explore an unsuspected technological territory : the world of gaming technology applied for the military, law enforcement, education or even … research.What are we referring to? Video games can be very intensive, and they can provide a very immersive experience. Commercial video games almost always feature characters involved in war or fighting actions which makes them an ideal tool for … real military training.”Read More
|
Do Universal Translators Already Exist?
By Martin Rupp
 “In this article, we will introduce the existing state-of-the-art in portative translating machines, for example small devices able to help English speaking tourists to dialog ‘in real-time’ with Russian speaking people (or the other way round).Imagine that you - an English speaker - have to visit Moscow or Saint-Petersburg. Wouldn’t it be nice that you can just ask help from some local people in their own language - Russian? Wouldn’t it be nice that they could hear the questions as you speak on your smartphone or tablet or laptop? Finally wouldn’t it be nice that they also can dialog with you and that their answers get translated to you in an equivalent way, allowing you to dialog with them?The ‘real-time’ translator has been abundantly featured in sci-fi literature and films for example, with the ability for a space traveler to dialog with locals from another world, in their native language, without knowing anything of it….”Read More
“In this article, we will introduce the existing state-of-the-art in portative translating machines, for example small devices able to help English speaking tourists to dialog ‘in real-time’ with Russian speaking people (or the other way round).Imagine that you - an English speaker - have to visit Moscow or Saint-Petersburg. Wouldn’t it be nice that you can just ask help from some local people in their own language - Russian? Wouldn’t it be nice that they could hear the questions as you speak on your smartphone or tablet or laptop? Finally wouldn’t it be nice that they also can dialog with you and that their answers get translated to you in an equivalent way, allowing you to dialog with them?The ‘real-time’ translator has been abundantly featured in sci-fi literature and films for example, with the ability for a space traveler to dialog with locals from another world, in their native language, without knowing anything of it….”Read More
|
How RADAR and Artificial Intelligence Allow us to Detect Finger-Counting-Based Gestures
By Martin Rupp
 “In what follows we will demonstrate how neural networks, and especially Convolution Neural networks can be used to perform the automatic detection of a human gesture by using RADAR technologies.The goal of the concept proof is to show that a pulse radar which is generally considered as affordable and which can be embedded in cars or homes can be used to automatically detect human gestures. Here: finger based gestures. The application of such systems can be multiple. In a car, this can be used as an additional way of interfacing the car controls, eg as an alternative to voice as a UI. A given gesture would be interpreted by the onboard computer of the car as a specific command such as “put the car stereo on”, “give me latest traffic news” etc… A driver may find it easier and faster to use gestures to communicate with the car computer rather than using voice commands which are not always well interpreted by the car system.”Read More
“In what follows we will demonstrate how neural networks, and especially Convolution Neural networks can be used to perform the automatic detection of a human gesture by using RADAR technologies.The goal of the concept proof is to show that a pulse radar which is generally considered as affordable and which can be embedded in cars or homes can be used to automatically detect human gestures. Here: finger based gestures. The application of such systems can be multiple. In a car, this can be used as an additional way of interfacing the car controls, eg as an alternative to voice as a UI. A given gesture would be interpreted by the onboard computer of the car as a specific command such as “put the car stereo on”, “give me latest traffic news” etc… A driver may find it easier and faster to use gestures to communicate with the car computer rather than using voice commands which are not always well interpreted by the car system.”Read More
|
Tokenization and NIST
By Martin Rupp
 “In this article, we will review some of the constraints of a tokenization solution when it comes to FIPS and more generally, NIST considerations”Read More
“In this article, we will review some of the constraints of a tokenization solution when it comes to FIPS and more generally, NIST considerations”Read More
|
How the Internet Of Things can save lives
By Martin Rupp
 “In this blog we will explore an interesting aspect of the IoT: the fact that many IoT devices can actually save lives. Of course Devices designed for medical usage such as blood pressure monitoring sensors etc… are - by design - saving lives but other devices with various usages in various environments can also be seen as contributing to ‘save lives’.”Read More
“In this blog we will explore an interesting aspect of the IoT: the fact that many IoT devices can actually save lives. Of course Devices designed for medical usage such as blood pressure monitoring sensors etc… are - by design - saving lives but other devices with various usages in various environments can also be seen as contributing to ‘save lives’.”Read More
|
Hyper-Automation
By Martin Rupp
 “This is a term you will hear more and more: hyperautomation. Basically, hyperautomation relates to a “conglomerate” of technologies ranging from RPA (Robotic Process Automation) to machine learning. Robotic process automation is based on robotic digital workers. It is sometimes referred to as ‘software robotics’. It is one of the pillars of Hyper-Automation. ”Read More
“This is a term you will hear more and more: hyperautomation. Basically, hyperautomation relates to a “conglomerate” of technologies ranging from RPA (Robotic Process Automation) to machine learning. Robotic process automation is based on robotic digital workers. It is sometimes referred to as ‘software robotics’. It is one of the pillars of Hyper-Automation. ”Read More
|
Key differences between Artificial Intelligence and Machine Learning
By Martin Rupp
 “In this article we wish to discuss fundamental and even axiomatic questions about the true nature of what is known as Artificial Intelligence or A.I and how it differs from its most common representation, Machine Learning (ML). Artificial Intelligence is everywhere now, in every talk-show, in the news, in the program of the most competitive universities, schools or companies. But what is really Artificial Intelligence? ”Read More
“In this article we wish to discuss fundamental and even axiomatic questions about the true nature of what is known as Artificial Intelligence or A.I and how it differs from its most common representation, Machine Learning (ML). Artificial Intelligence is everywhere now, in every talk-show, in the news, in the program of the most competitive universities, schools or companies. But what is really Artificial Intelligence? ”Read More
|
Why we need Hardware Security Modules (HSMs)
By Martin Rupp
 “HSM stands for Hardware Security Module, a piece of hardware where some cryptographic operations can be securely performed. What is an HSM? What is it good for ? And why do we need it?”Read More
“HSM stands for Hardware Security Module, a piece of hardware where some cryptographic operations can be securely performed. What is an HSM? What is it good for ? And why do we need it?”Read More
|
The A.I Algorithms we Borrowed From Nature
By Martin Rupp
 “Artificial Intelligence is usually conceived as the manifestation of any non-Human intelligence, this later one is described in opposition as “natural” intelligence.Humans are not the only creatures living on earth which are capable of computing and demonstrating intelligence. Fortunately enough for us, human intelligence is usually regarded as - by far - the highest in their environment.Nevertheless,other living creatures as insects or animals are known to demonstrate various forms of organizations and “collective” intelligence that fall into the Artificial Intelligence category.”Read More
“Artificial Intelligence is usually conceived as the manifestation of any non-Human intelligence, this later one is described in opposition as “natural” intelligence.Humans are not the only creatures living on earth which are capable of computing and demonstrating intelligence. Fortunately enough for us, human intelligence is usually regarded as - by far - the highest in their environment.Nevertheless,other living creatures as insects or animals are known to demonstrate various forms of organizations and “collective” intelligence that fall into the Artificial Intelligence category.”Read More
|
An overview of Cyber-Physical System (CPS) PART II - REFLEXIONS ABOUT CPS & THEIR MANAGEMENT
By Martin Rupp
 “The notion of CPS is closely related to the area of robotics and sensor networks using computational intelligence. CybAn overview of mini-drone technology
“The notion of CPS is closely related to the area of robotics and sensor networks using computational intelligence. CybAn overview of mini-drone technology
By Martin Rupp
“That is something you probably have not seen coming, but here we want to give you the fresher news in technology, and so we have to update you about a rising trend: the rise of the insect robotic drones, or micro drones! A drone is … already an insect, it’s of course the male honey bee… the term has been popularized recently to describe the quad-copters devices and other similar unmanned planes. Now there are really drone drones, e.g. insect robots, often radio-controlled.”er-physical Systems build the link between ‘abstract’ computational and ‘real’ physical components by using ‘smart’ systems, increasing the autonomy, adaptability, efficiency, reliability, and functionality of devices”Read More
|
An overview of Cyber-Physical System (CPS) PART I - Introduction and main Considerations about CPS
By Martin Rupp
 “In that article, we shall go through a complex and very important notion: the Cyber-Physical Systems (CPS). CPS is not a very well known term but it is gaining more and more importance for all key players in I.T and technology in general.In what follows we will explain what is CPS and describe what evolution could be expected regarding the systems which are described by this concept.”Read More
“In that article, we shall go through a complex and very important notion: the Cyber-Physical Systems (CPS). CPS is not a very well known term but it is gaining more and more importance for all key players in I.T and technology in general.In what follows we will explain what is CPS and describe what evolution could be expected regarding the systems which are described by this concept.”Read More
|
An overview of mini-drone technology
By Martin Rupp
 “That is something you probably have not seen coming, but here we want to give you the fresher news in technology, and so we have to update you about a rising trend: the rise of the insect robotic drones, or micro drones! A drone is … already an insect, it’s of course the male honey bee… the term has been popularized recently to describe the quad-copters devices and other similar unmanned planes. Now there are really drone drones, e.g. insect robots, often radio-controlled.”Read More
“That is something you probably have not seen coming, but here we want to give you the fresher news in technology, and so we have to update you about a rising trend: the rise of the insect robotic drones, or micro drones! A drone is … already an insect, it’s of course the male honey bee… the term has been popularized recently to describe the quad-copters devices and other similar unmanned planes. Now there are really drone drones, e.g. insect robots, often radio-controlled.”Read More
|
EMV and Quantum Crypto
By Martin Rupp
 “Post-Quantum crypto refers to a class of cryptographic algorithms and methods that are deemed to resist Quantum Computing attacks. Quantum computing uses quantum physics and works differently from “traditional” digital computers. Two quantum algorithms: Shor's Algorithm and Grover’s algorithm allow performing powerful quantum attacks against, respectively, asymmetric and symmetric cryptographic algorithms, which are widely used in the industry. RSA, 3-DES or AES, for instance, are considered to be vulnerable to quantum computing."Read More
“Post-Quantum crypto refers to a class of cryptographic algorithms and methods that are deemed to resist Quantum Computing attacks. Quantum computing uses quantum physics and works differently from “traditional” digital computers. Two quantum algorithms: Shor's Algorithm and Grover’s algorithm allow performing powerful quantum attacks against, respectively, asymmetric and symmetric cryptographic algorithms, which are widely used in the industry. RSA, 3-DES or AES, for instance, are considered to be vulnerable to quantum computing."Read More
|
Could LISP Machines do a comeback
By Martin Rupp
 “In this article, we will go through a class of computers known as the LISP machines. These machines have been built mainly in the 80’s in order to create computers equipped with (machine) Artificial Intelligence.In the rest of that paper, we will refer to the term A.I as machine-based artificial intelligence or “pseudo”-Artificial Intelligence since we consider that the rigorous definition of ‘real’ Artificial Intelligence is non-human “active” intelligence.”Read More
“In this article, we will go through a class of computers known as the LISP machines. These machines have been built mainly in the 80’s in order to create computers equipped with (machine) Artificial Intelligence.In the rest of that paper, we will refer to the term A.I as machine-based artificial intelligence or “pseudo”-Artificial Intelligence since we consider that the rigorous definition of ‘real’ Artificial Intelligence is non-human “active” intelligence.”Read More
|
Understanding Utimaco's library and toolsuite of Post Quantum Proof Algorithms
By Martin Rupp
 “NIST, the National Institute of Standards and Technology, whose role is to maintain an adequate and up-to-date set of technological standards, has offered a "hybrid" approach to help the migration to Post-Quantum crypto altogether with NIST certifications.It is important to remember that PQC certification is still an ongoing process at NIST. Therefore, the "hybrid" approach is the recommended method to achieve a NIST certification.What exactly is the "hybrid" approach?”Read More
“NIST, the National Institute of Standards and Technology, whose role is to maintain an adequate and up-to-date set of technological standards, has offered a "hybrid" approach to help the migration to Post-Quantum crypto altogether with NIST certifications.It is important to remember that PQC certification is still an ongoing process at NIST. Therefore, the "hybrid" approach is the recommended method to achieve a NIST certification.What exactly is the "hybrid" approach?”Read More
|
Everything you wanted to know about EMV (but you were too afraid to ask)
By Martin Rupp
 “With almost a billion of EMV certified payment cards all around the world, EMV is a major financial actor, while being a normative body. The EMV norm is a powerful instrument of ‘politics’ for the major card brands inside EMV and they have created the system of the ‘EMV deadlines’ where bank from countries are being pressurized to provide, before a given date, a domestic EMV implementation, agreed by their respective national central banks. Failure to comply with such norms would result in EMV no longer willing to take the burden of the fraud for these non-compliant banks.”Read More
“With almost a billion of EMV certified payment cards all around the world, EMV is a major financial actor, while being a normative body. The EMV norm is a powerful instrument of ‘politics’ for the major card brands inside EMV and they have created the system of the ‘EMV deadlines’ where bank from countries are being pressurized to provide, before a given date, a domestic EMV implementation, agreed by their respective national central banks. Failure to comply with such norms would result in EMV no longer willing to take the burden of the fraud for these non-compliant banks.”Read More
|
What is the future for Bitcoin ATMs and Bitcoin Credit Cards?
By Martin Rupp
 “In that article we will dig into the fascinating world of the Bitcoins ATMs and the Bitcoins credit cards. We assume this is an area which is badly known to the reader. But as we want to give you the latest news in science and technology, here we are!”Read More
“In that article we will dig into the fascinating world of the Bitcoins ATMs and the Bitcoins credit cards. We assume this is an area which is badly known to the reader. But as we want to give you the latest news in science and technology, here we are!”Read More
|
A brief overview of Cyberpunks and Cypherpunks movements
By Martin Rupp
 “We want this article to give the readers an interesting and comprehensive overview of a badly known movement which is linking technology, cryptographic and politics, this is the Cyberpunk movement. Cyberpunk is at start an artistic movement and features a dystopian future where life is in general quite hard and where the level of technology is important and especially using cybernetics, robotics and artificial intelligence. ”Read More
“We want this article to give the readers an interesting and comprehensive overview of a badly known movement which is linking technology, cryptographic and politics, this is the Cyberpunk movement. Cyberpunk is at start an artistic movement and features a dystopian future where life is in general quite hard and where the level of technology is important and especially using cybernetics, robotics and artificial intelligence. ”Read More
|
Why developers should never use the C# System.Random class
By Martin Rupp
 “Any developer has probably already needed at least once to call a random function during the development of a program or a library. Most programming languages possess their own random generators. Here we will study the System.Random.Rand RNG and how it behaves in terms of randomness quality.”Read More
“Any developer has probably already needed at least once to call a random function during the development of a program or a library. Most programming languages possess their own random generators. Here we will study the System.Random.Rand RNG and how it behaves in terms of randomness quality.”Read More
|
How RSA Works
By Martin Rupp
 “RSA is the root of all asymmetric key cryptographic algorithms. It is asymmetric because the decryption key is different from the encryption key.RSA was first published in 1977.RSA uses basic properties of modular arithmetic , that is to say the arithmetic operations in a finite congruence ring , namely the ring of integers modulo n, where n is an integer > 0.”Read More
“RSA is the root of all asymmetric key cryptographic algorithms. It is asymmetric because the decryption key is different from the encryption key.RSA was first published in 1977.RSA uses basic properties of modular arithmetic , that is to say the arithmetic operations in a finite congruence ring , namely the ring of integers modulo n, where n is an integer > 0.”Read More
|
An Overview Of The Microsoft Robotics Developer Studio
By Martin Rupp
 “MRDS provides a platform for developing applications involved with robotics and basic service components in order to allow every designer with an interest in developing robots to easily program the necessary procedures to run robot hardware, without being restricted by the underlying complexity of the hardware system.”Read More
“MRDS provides a platform for developing applications involved with robotics and basic service components in order to allow every designer with an interest in developing robots to easily program the necessary procedures to run robot hardware, without being restricted by the underlying complexity of the hardware system.”Read More
|
Why all the Space Probes we send to Venus will never use Digital Technology
By Martin Rupp
 “Digital technology was invented in the late 70’s. They are based on semiconductors technologies which allow the creation of digital circuits and by extension digital chips or digital processors(...)”Read More
“Digital technology was invented in the late 70’s. They are based on semiconductors technologies which allow the creation of digital circuits and by extension digital chips or digital processors(...)”Read More
|