SCIENTIFIC AND COMPUTER DEVELOPMENT BLOG
1|2
|
Developing a custom flight simulation for a
mission from Earth to Triton
By Martin Rupp
06/January/2024
 In this scenario we simulate sending a cubesat from Earth to Triton. As a first step, a heavy
launcher sends the mothership to Neptune, using gravity-assisted propulsion. The second
step consists of the mother ship detaching the cubesat as she is injected into Neptune’s
orbit, computing the orbit transfer, and sending the cubesat into Triton’s orbit. The goal of the
mission being to observe Triton from its orbit.
In this scenario we simulate sending a cubesat from Earth to Triton. As a first step, a heavy
launcher sends the mothership to Neptune, using gravity-assisted propulsion. The second
step consists of the mother ship detaching the cubesat as she is injected into Neptune’s
orbit, computing the orbit transfer, and sending the cubesat into Triton’s orbit. The goal of the
mission being to observe Triton from its orbit.
Read More
|
Fleet cards, Fuel cards - Transition from 3DES to AES
By Martin Rupp
29/November/2023
 An overlook at Fuel cards
Fuel cards are issued by special companies such as Wex Inc, Fuelman or Comdata, for example. Additionally, they can also be issued by banks following a credit card payment scheme (Visa, MasterCard,...)
Fleet fuel cards allow company employees to purchase fuel and repair services inside a network of partner gas stations (usually most of the gas stations in the US accept these cards) and other merchants.
The fleet operator of a company can monitor transactions and make sure there is no fraud or that cards are wrongly used for other purposes. Additionally Fleet Fuel cards often offer interesting rebates and loyalty programs.
An overlook at Fuel cards
Fuel cards are issued by special companies such as Wex Inc, Fuelman or Comdata, for example. Additionally, they can also be issued by banks following a credit card payment scheme (Visa, MasterCard,...)
Fleet fuel cards allow company employees to purchase fuel and repair services inside a network of partner gas stations (usually most of the gas stations in the US accept these cards) and other merchants.
The fleet operator of a company can monitor transactions and make sure there is no fraud or that cards are wrongly used for other purposes. Additionally Fleet Fuel cards often offer interesting rebates and loyalty programs.
Read More
|
An overview of biological and computer virology
By Martin Rupp
28/November/2023
 The pandemic named "COVID-19" has dramatically raised the whole world about the existence of viruses that are deadly for humankind. In this article, we will explain to the reader what biological and computer viruses are and by which mechanisms they can be linked together.
The pandemic named "COVID-19" has dramatically raised the whole world about the existence of viruses that are deadly for humankind. In this article, we will explain to the reader what biological and computer viruses are and by which mechanisms they can be linked together.
Read More
|
An overview of AI and cybersecurity: why we need AI(ML) in the cybersecurity world
By Martin Rupp
26/November/2023
 As we saw in the first part, AI and more precisely ML (let's only refer to AI as ML in what follows) aim at sorting, classifying, or regressing data and performing tasks in efficient ways that are proper to machines and that humans cannot perform because the data may be too huge and the analysis may be too complex.
There are two ways to be clever: either having a very smart way of reasoning or knowing a lot of things. In ML terms, the smart way of reasoning is the model and the knowledge is the data that has been learned. ML algorithms can combine both but most often this is their capacity to treat and learn from huge volumes of data which makes a difference.
As we saw in the first part, AI and more precisely ML (let's only refer to AI as ML in what follows) aim at sorting, classifying, or regressing data and performing tasks in efficient ways that are proper to machines and that humans cannot perform because the data may be too huge and the analysis may be too complex.
There are two ways to be clever: either having a very smart way of reasoning or knowing a lot of things. In ML terms, the smart way of reasoning is the model and the knowledge is the data that has been learned. ML algorithms can combine both but most often this is their capacity to treat and learn from huge volumes of data which makes a difference.
Read More
|
What are the main differences between X9.24-2-2016 and X9.24-1-2017?
By Martin Rupp
25/November/2023
 The X9.24 norm “Retail Financial Services Symmetric Key Management“ is split into three distinct parts. Part 1 (2016) deals with symmetric key management using symmetric cryptography techniques, while Part 2 (2017) deals with symmetric key management using asymmetric cryptography. Lastly, Part 3 (2017) is an aside that deals with the derived unique key per transaction (DUKPT) algorithm.
In what follows, we explain the main differences between the management of symmetric keys using respectively symmetric and asymmetric techniques, according to the X9.24 norm.
The X9.24 norm “Retail Financial Services Symmetric Key Management“ is split into three distinct parts. Part 1 (2016) deals with symmetric key management using symmetric cryptography techniques, while Part 2 (2017) deals with symmetric key management using asymmetric cryptography. Lastly, Part 3 (2017) is an aside that deals with the derived unique key per transaction (DUKPT) algorithm.
In what follows, we explain the main differences between the management of symmetric keys using respectively symmetric and asymmetric techniques, according to the X9.24 norm.
Read More
|
The benefits of partitionable HSMs
By Martin Rupp
24/November/2023
 Severe competition and increasingly volatile markets push CIOs and CISOs to rethink their IT and bring costs down. At the same time, many banks opt for a service platform strategy, which requires the banks' IT in general, and the crypto architecture in specific to be more flexible and sophisticated. In this article, we will look at how partitioned HSMs can reduce the total cost of ownership and at the same time make the architecture more flexible and able to rapidly embrace new applications.
Severe competition and increasingly volatile markets push CIOs and CISOs to rethink their IT and bring costs down. At the same time, many banks opt for a service platform strategy, which requires the banks' IT in general, and the crypto architecture in specific to be more flexible and sophisticated. In this article, we will look at how partitioned HSMs can reduce the total cost of ownership and at the same time make the architecture more flexible and able to rapidly embrace new applications.
Read More
|
Want a faster payment HSM?
By Martin Rupp
23/November/2023
 HSMs are primarily focused on security but they also need to be fast. crypto operations are very demanding operations and require important processing power. Crypto processors used by the HSMs are fast because the cryptographic routines are implemented in the hardware directly but they need to cope with eventual high-volume requests.
Here we look at the AT1000 and check what it takes to be a fast payment HSM.
HSMs are primarily focused on security but they also need to be fast. crypto operations are very demanding operations and require important processing power. Crypto processors used by the HSMs are fast because the cryptographic routines are implemented in the hardware directly but they need to cope with eventual high-volume requests.
Here we look at the AT1000 and check what it takes to be a fast payment HSM.
Read More
|
Virtual and Augmented Reality
By Martin Rupp
22/November/2023
 This article will share with you the latest information about two powerful and interconnected technologies: Virtual Reality and Augmented Reality.
For many readers, the two terms may look to be identical but they are not. They are in fact dual of each other.
Virtual Reality describes generally an “artificial” digital or numerical universe in which we are plunged. The “3D games’ that appeared in the 80’s and the 90’s are a perfect example of that virtual reality.
This article will share with you the latest information about two powerful and interconnected technologies: Virtual Reality and Augmented Reality.
For many readers, the two terms may look to be identical but they are not. They are in fact dual of each other.
Virtual Reality describes generally an “artificial” digital or numerical universe in which we are plunged. The “3D games’ that appeared in the 80’s and the 90’s are a perfect example of that virtual reality.
Read More
|
KRDs and KDHs in the X9.24-2-2016 Norm
By Martin Rupp
21/November/2023
 KRDs and KDHs are essential notions in the context of the X9.24-2 norm. A KRD is a key receiving device, while a KDH is a key distribution host.
The X9.24-2-2016 norm deals with the transportation of symmetric keys using asymmetric cryptography. Therefore, this norm considers two kinds of devices:
A KDH that provides the key, which is typically an HSM
A device that receives the keys, such as a PED (PIN Entry Device) from an ATM or EFT-POS
The KRD and KDH are the main components in the X9.24-2 norm aside from a possible PKI system with a CA.
KRDs and KDHs are essential notions in the context of the X9.24-2 norm. A KRD is a key receiving device, while a KDH is a key distribution host.
The X9.24-2-2016 norm deals with the transportation of symmetric keys using asymmetric cryptography. Therefore, this norm considers two kinds of devices:
A KDH that provides the key, which is typically an HSM
A device that receives the keys, such as a PED (PIN Entry Device) from an ATM or EFT-POS
The KRD and KDH are the main components in the X9.24-2 norm aside from a possible PKI system with a CA.
Read More
|
The Specificity of the Requirements
for SCD with Asymmetric Keys According to X9.24-2-2016
By Martin Rupp
20/November/2023
 SCDs are secure cryptographic devices compliant with the requirements defined in the ISO 13491-1 and ANS X9.24 Part 1 norms. They are widely used within the scope of the X9.24 standard.
SCDs are secure cryptographic devices compliant with the requirements defined in the ISO 13491-1 and ANS X9.24 Part 1 norms. They are widely used within the scope of the X9.24 standard.
Read More
|
The PKCS #8 Ciphered Private Key format
By Martin Rupp
19/November/2023
 PKCS #8 is a part of the PKCS standard (Public Key Cryptography Standards). It defines a ‘syntax’ allowing the storage of private key information.
The PKCS #8 syntax can only be considered a key block when dealing with a ciphered private key. In such a format, a key will be ciphered by a symmetric algorithm which can be triple-DES or AES. The (symmetric) key that ciphers the data is generated by a key derivation scheme (pbkdf2, for example) from a password.
PKCS #8 is a part of the PKCS standard (Public Key Cryptography Standards). It defines a ‘syntax’ allowing the storage of private key information.
The PKCS #8 syntax can only be considered a key block when dealing with a ciphered private key. In such a format, a key will be ciphered by a symmetric algorithm which can be triple-DES or AES. The (symmetric) key that ciphers the data is generated by a key derivation scheme (pbkdf2, for example) from a password.
Read More
|
The Challenges of 5G
By Martin Rupp
18/November/2023
 There is currently a growing public debate about 5G. Anyway for a lot of people in the world, who still do not have access to 4G, this seems to be relatively irrelevant. Let us see what is exactly 5G and why we should care about it.
5G is a term that refers to the fifth-generation technology standard for internet mobile networks.
It is now a custom to denote each new version of such technology by an increment following the term ‘G’ (as for Generation)
Most Mobile Network Operators in the Western world - and especially in the USA - have begun deploying 5G worldwide in 2019.
There is currently a growing public debate about 5G. Anyway for a lot of people in the world, who still do not have access to 4G, this seems to be relatively irrelevant. Let us see what is exactly 5G and why we should care about it.
5G is a term that refers to the fifth-generation technology standard for internet mobile networks.
It is now a custom to denote each new version of such technology by an increment following the term ‘G’ (as for Generation)
Most Mobile Network Operators in the Western world - and especially in the USA - have begun deploying 5G worldwide in 2019.
Read More
|
The Amazing World of the “non-standard” Search Engines
By Martin Rupp
17/November/2023
 In this article, we will explore an amazing world that may be unknown to the reader: the world of 'non-standard' search engines.
By 'non-standard', we mean that they act differently than the 'traditional' text-based search engines such as Google, Yahoo, Bing, and others. Some do not use text as keywords but multimedia elements instead, such as pictures, sounds, or videos for instance. Some others allow searching in strange locations such as IoT devices. We wish here to give the reader a tour of these uncommon search engines.
In this article, we will explore an amazing world that may be unknown to the reader: the world of 'non-standard' search engines.
By 'non-standard', we mean that they act differently than the 'traditional' text-based search engines such as Google, Yahoo, Bing, and others. Some do not use text as keywords but multimedia elements instead, such as pictures, sounds, or videos for instance. Some others allow searching in strange locations such as IoT devices. We wish here to give the reader a tour of these uncommon search engines.
Read More
|
Are Mongodb Databases Really Secure?
By Martin Rupp
16/November/2023
 In that article we aim at looking at the data about the security of Mongo database - a very popular no-SQL database - which is widely used all over the world.
MongoDB has suffered from many bad stories where the databases of many mongoDB users were hacked because of what is known as a ‘no-security configuration’ by default.
Here we wish to look at the facts and investigate if Mongo Database is really secure or not.
In that article we aim at looking at the data about the security of Mongo database - a very popular no-SQL database - which is widely used all over the world.
MongoDB has suffered from many bad stories where the databases of many mongoDB users were hacked because of what is known as a ‘no-security configuration’ by default.
Here we wish to look at the facts and investigate if Mongo Database is really secure or not.
Read More
|
Autopsy of a BYOK solution
By Martin Rupp
15/November/2023
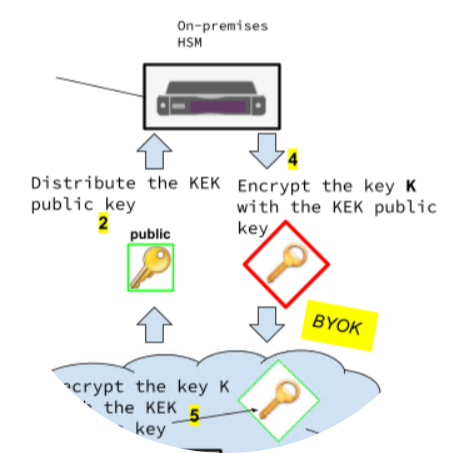 KMS means Key Management Service. Usually, it is a secure and resilient service based on hardware security modules that have been validated under FIPS 140-2. Each cloud provider has its own KMS.
KMS means Key Management Service. Usually, it is a secure and resilient service based on hardware security modules that have been validated under FIPS 140-2. Each cloud provider has its own KMS.
Read More
|
A Guide to the A.I. Cards and A.I. Processors
By Martin Rupp
14/November/2023
 As AI is invading more and more of our daily lives, a new type of hardware is making its way: the AI-powered processors, that is to say, the processors specially designed to run Artificial Intelligence algorithms.
As AI is invading more and more of our daily lives, a new type of hardware is making its way: the AI-powered processors, that is to say, the processors specially designed to run Artificial Intelligence algorithms.
Read More
|
A basic ciphering algorithm using cyclotomic fields
By Martin Rupp
04/August/2023
Description of a basic cipher using the concept of invertible unit in a cyclotomic field.
Read More
|
General Concept of Runtime Application Self-Protection (RASP)
By Martin Rupp
09/July/2023
 Here we demonstrate the features of a sentinel system in a mobile context. This system
might also be referred to as Runtime Application Self-Protection or simply RASP.
A sentinel system is a background process that is usually not easily detectable. It
monitors “in real time” several parameters associated with the mobile operating system
and the applications it protects.
For instance, a sentinel could detect attempts to use an emulator or a debugger. It could
also check the integrity of files and scan the memory (flash, RAM, EEPROM) for
viruses. A sentinel would have two parts: a "detector" part and a "reactor" part. The
detector would signal that it detected possible attempts to attack the application while a
reactor would take the proper decision following that information.
Here we demonstrate the features of a sentinel system in a mobile context. This system
might also be referred to as Runtime Application Self-Protection or simply RASP.
A sentinel system is a background process that is usually not easily detectable. It
monitors “in real time” several parameters associated with the mobile operating system
and the applications it protects.
For instance, a sentinel could detect attempts to use an emulator or a debugger. It could
also check the integrity of files and scan the memory (flash, RAM, EEPROM) for
viruses. A sentinel would have two parts: a "detector" part and a "reactor" part. The
detector would signal that it detected possible attempts to attack the application while a
reactor would take the proper decision following that information.
Read More
|
A Comparison Between Cryptocurrencies and Digital Dollar
By Martin Rupp
11/May/2023
 In that article, we shall study the differences between the cryptocurrencies and what is announced as the national central bank-backed digital dollar.
The digital dollar - as a digital fiat currency - does not exist yet, nevertheless, there are many hints about the technologies that it may use and how it will be confronted with the actual cryptocurrencies.
In that article, we shall study the differences between the cryptocurrencies and what is announced as the national central bank-backed digital dollar.
The digital dollar - as a digital fiat currency - does not exist yet, nevertheless, there are many hints about the technologies that it may use and how it will be confronted with the actual cryptocurrencies.
Read More
|
A Deep Introduction to the Blockchain
By Martin Rupp
29/April/2023
 Blockchain technology is everywhere and the term is used every day by many sales managers, engineers, specialists and developers in the context of their work. But do they really and can they really define what blockchain technology is with enough accuracy? The goal of that article is to bring them some insight into the topic.
Blockchain technology is everywhere and the term is used every day by many sales managers, engineers, specialists and developers in the context of their work. But do they really and can they really define what blockchain technology is with enough accuracy? The goal of that article is to bring them some insight into the topic.
Read More
|
Anatomy of Modern Bank Robberies: Proof Why PIN Protection and KeyBlocks are Important
By Martin Rupp
04/December/2022
 In this article, we explain how compromising the PIN of a customer’s prepaid debit card may lead to catastrophic losses for a bank and why it is so important to protect their data.
In this article, we explain how compromising the PIN of a customer’s prepaid debit card may lead to catastrophic losses for a bank and why it is so important to protect their data.
We will analyze two ATM “cash-out" hacking stories that are linked to prepaid debit cards and explain why these frauds could have been prevented if the correct technologies had been used.
HSMs aren’t just needed “because of PCI-DSS requirements" which do not explicitly require the use of HSMs. Today, for Fintech companies (and everywhere else as well) penetration or intrusion testing is part of the enterprise culture. Cryptography, encryption, norms, using FIPS-140 security-evaluated products are just “routine."
Read More
|
Why Banks Should Care More About A.I. Attacks
By Martin Rupp
 "Welcome to the 21st century, where science-fiction looks increasingly less like fiction!
"Welcome to the 21st century, where science-fiction looks increasingly less like fiction!
A new crypto-threat has emerged from the depths of science and technology, named “neural cryptography."
As with everything disrupting, neural cryptography isn’t so new. In 1995, Sebastien Dourlens, a French researcher in cryptography, pioneered it in some ways, including in his master Ph.D. thesis, by using a neural network (quite simple at the time) to perform cryptanalysis of the DES cipher.
Neural cryptography isn’t a well-established discipline. It relates to the use of AI and mainly neural networks in cryptanalysis techniques.“
Read More
|
Analysis of the Legendre Random Number Generator
By Martin Rupp
“ we see that the Legendre RNG exhibits good randomness and passes the
statistical tests such as NIST or Dieharder. Legendre RNG may be considered as an acceptable
Random number generator.”
Read More
|